How digital badges can help you reveal information about people
What are Digital Badges?
Digital badges (also known as e-badges) are a validated indicator of accomplishment, skill, quality or interest that can be earned in various learning environments. In other words, it’s a certificate that “proves” that you have obtained some kind of skill/training and its validity is guaranteed by the authoring organization. Digital Badges are used very often and their popularity constantly increases, as the time goes by. They help people reinforce their CV or LinkedIn (or similar sites) profiles.
Why are they important in an OSINT investigation?
Due to their nature, digital badges are meant to be public. Otherwise, they cannot be publicly shared to potential employers, in order to verify the skills, the potential employee is claiming to possess. There are work-arounds to this like providing a code to the potential employer so that he/she can visit the site offering the digital badge and use this code for verification purposes, but let’s be honest…you don’t want to make it hard for an employer to verify things. Furthermore, people generally don’t want to use a nickname instead of their real name, because it won’t be easy to explain the connection between themselves and the nickname, plus it’s not considered “professional”. Of course, there are always exceptions, as we will see later. Last but not least, it is extremely easy and tempting to post your achievements with your professional (or other) network. In fact, these digital badge sites are constantly encouraging you to do so. For the above reasons, digital badges are left publicly available, most of the times containing real information about targets and provide information that help OSINT investigators in finding more leads.
Exploring how a digital badge can assist OSINT investigations
In order to showcase an example, I am going to use acclaim website by credly. This is one of the most famous digital badges issuing sites. Just run a google search query of
site:youracclaim.com/organizations/*/badges/
and start scrolling down to find big companies such as IBM (with 2336 different badges) and Huawei (with just 11 badges).
Digital badges (also known as e-badges) are a validated indicator of accomplishment, skill, quality or interest that can be earned in various learning environments. In other words, it’s a certificate that “proves” that you have obtained some kind of skill/training and its validity is guaranteed by the authoring organization. Digital Badges are used very often and their popularity constantly increases, as the time goes by. They help people reinforce their CV or LinkedIn (or similar sites) profiles.
Why are they important in an OSINT investigation?
Due to their nature, digital badges are meant to be public. Otherwise, they cannot be publicly shared to potential employers, in order to verify the skills, the potential employee is claiming to possess. There are work-arounds to this like providing a code to the potential employer so that he/she can visit the site offering the digital badge and use this code for verification purposes, but let’s be honest…you don’t want to make it hard for an employer to verify things. Furthermore, people generally don’t want to use a nickname instead of their real name, because it won’t be easy to explain the connection between themselves and the nickname, plus it’s not considered “professional”. Of course, there are always exceptions, as we will see later. Last but not least, it is extremely easy and tempting to post your achievements with your professional (or other) network. In fact, these digital badge sites are constantly encouraging you to do so. For the above reasons, digital badges are left publicly available, most of the times containing real information about targets and provide information that help OSINT investigators in finding more leads.
Exploring how a digital badge can assist OSINT investigations
In order to showcase an example, I am going to use acclaim website by credly. This is one of the most famous digital badges issuing sites. Just run a google search query of
site:youracclaim.com/organizations/*/badges/
and start scrolling down to find big companies such as IBM (with 2336 different badges) and Huawei (with just 11 badges).
You ‘d think that only IT related companies are using this site, but if you search around you will find from accounting to nursing organizations, issuing their own badges. Another way to find organizations using acclaim, is to create an account and then use the search bar on the top of the site, as seen below:
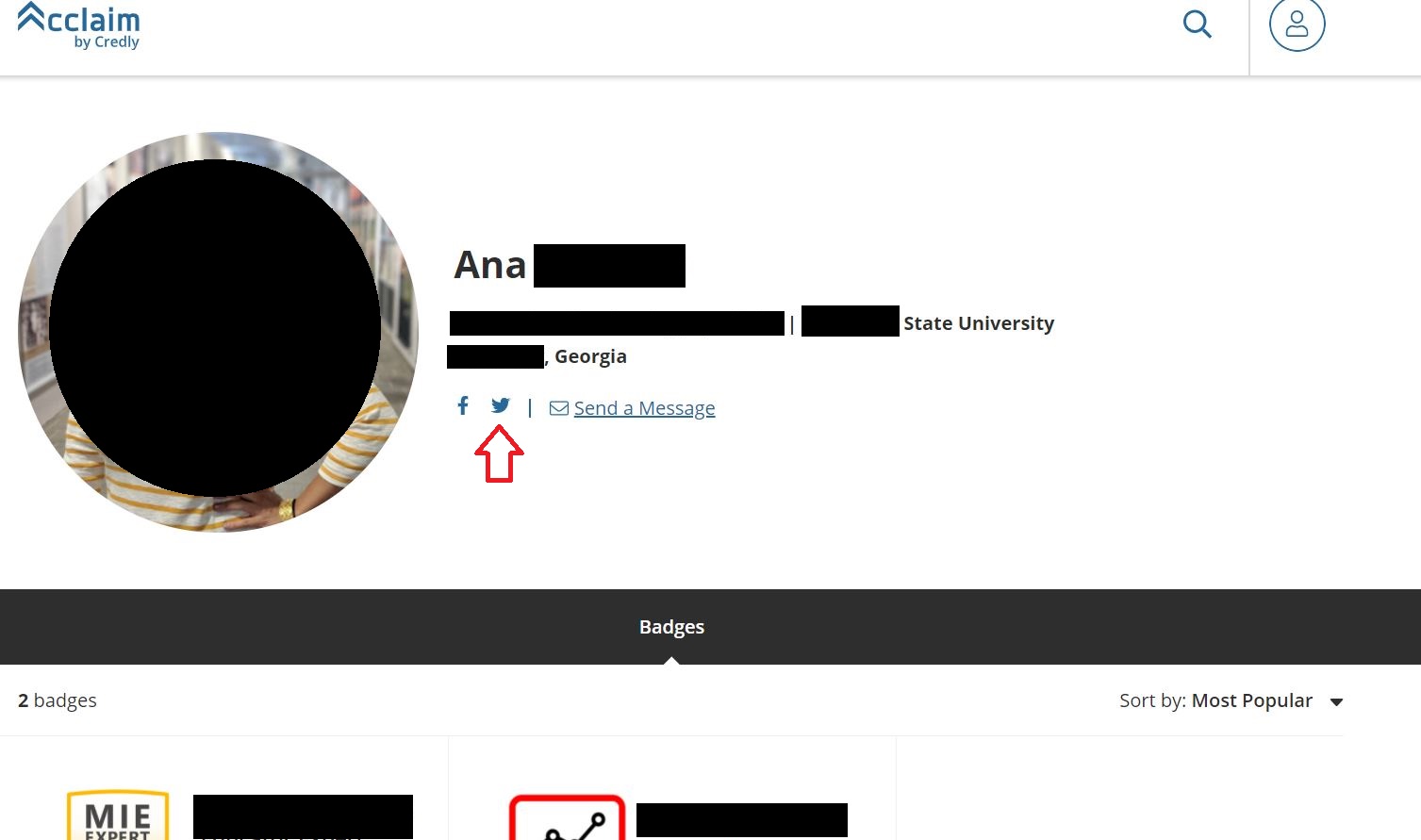
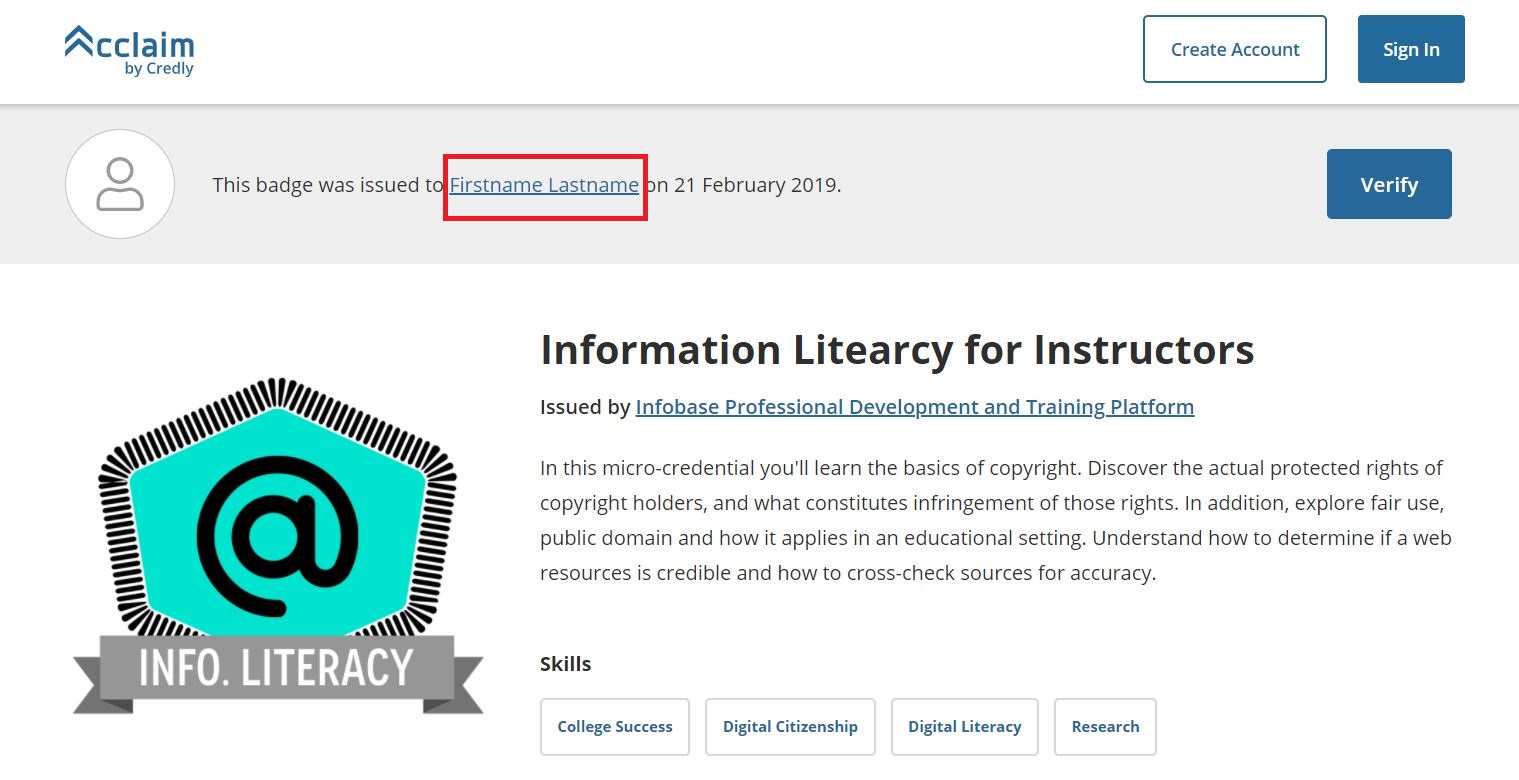
Anyway, if we click on the profile picture on the upper right corner, we can then click “View Profile” and we will be redirected to our publicly accessible profile. The structure of the url is https://www.youracclaim.com/users/firstname-lastname/badges, where firstname and lastname are the first and last names we used when signing in the platform (actually there is a profile using “Firstname Lastname” as his/her profile full name, LOL!).
Experimenting with changing the first/last name fields of the url with a totally random name, we get the following result:
Experimenting with changing the first/last name fields of the url with a totally random name, we get the following result:
By just manipulating the first name and last name in the url, we found a job position (red box), a University where this person studied (blue box), place of residence (green line), three digital badges (yellow box) and a linked Facebook account!
You can understand that the rarer the name of our target, the better. That’s because there will be a lower chance that this is another one with the same name. Of course, if we are not in the initial stages of an investigation and we know more information about the target (e.g. a place of residence), we can easily verify this is indeed our target.
Now let’s suppose we would like to see people who have studied in the same State University as our random target. We are going to perform a quick little google dork with the query
site:youracclaim.com/users/ intext:"………… State University"
and get the results as shown below:
You can understand that the rarer the name of our target, the better. That’s because there will be a lower chance that this is another one with the same name. Of course, if we are not in the initial stages of an investigation and we know more information about the target (e.g. a place of residence), we can easily verify this is indeed our target.
Now let’s suppose we would like to see people who have studied in the same State University as our random target. We are going to perform a quick little google dork with the query
site:youracclaim.com/users/ intext:"………… State University"
and get the results as shown below:
That did go well. Let’s hit another random name from the results and see what we can find.
This time we got a twitter profile also (red arrow) and a profile image. Sweet! If you want to download the profile image, just right click it and “open image in new tab”. In the new tab, right-click and download the image. Unfortunately, exif data seem to have been removed. But we can still reverse search the images! Interestingly, clicking at the Facebook profile button, we are told by Facebook, that we cannot access this FB page/group/whatever due to being restricted to specific audience or removed. Meaning, we wouldn’t be able to find this page easily otherwise, since it has either been deleted or became private!
Now looking at the url of this profile, we don’t have a first name and a last name. In their place, there is only a 4-digit number! It resembles a birthdate, which might be the real deal looking at the profile picture, but we can’t be sure unless further investigation is conducted. We manipulate the url and insert the format we ‘ve seen above using first and last name of this person. Hitting “enter” we are redirected to another profile with the same name but different info.
Now looking at the url of this profile, we don’t have a first name and a last name. In their place, there is only a 4-digit number! It resembles a birthdate, which might be the real deal looking at the profile picture, but we can’t be sure unless further investigation is conducted. We manipulate the url and insert the format we ‘ve seen above using first and last name of this person. Hitting “enter” we are redirected to another profile with the same name but different info.
I will explain immediately why this is important. We switch to a google search of
site:youracclaim.com/users/* "Ana ………..",
using the full name of our target(s). The results are as follows:
site:youracclaim.com/users/* "Ana ………..",
using the full name of our target(s). The results are as follows:
In the results we see only one user with that name. How is that explained, since we found two of them? Clicking in the upper right corner of our profile, under the Settings --> Privacy and Security, we see that the profile can be set to “publicly visible”, but at the same time, it can be set to disallow search engines to index it.
So, our first Ana had both switched to “Allow”, but the other one had set the profile to be publicly visible (in order to share it with potential employees), but not to be included in searchable directories!
Now let’s switch search engines and try Yandex. Running the exact same query we get again only one result but different from the other two we have found!
Now let’s switch search engines and try Yandex. Running the exact same query we get again only one result but different from the other two we have found!
This one even has a middle name! Look closely at the query. If we use site:youracclaim.com/users/ followed by a full name in quotes, Yandex will not bring any results. But after using site:youracclaim.com followed by a full name in quotes, Yandex brought up results although google didn’t!
During experimenting, I had a curiosity to see if there was only a binary situation: either firstname-lastname or whatever in the url in its place. In this tutorial we can read “You can personalize your Acclaim profile URL (e.g. http://www.youracclaim.com/user/your-name)". So this is why our first Ana had a 4-digit number instead of a name. But until I figure this out, I searched around and found something also important. After doing some googling using
site:youracclaim.com/users/* intext:"John Smith",
which is a very common name, I ‘ve found 2-3 acclaim profiles with john-smith.e23bd433 or similar in the link (there is no such profile, it’s just the format I found).
During experimenting, I had a curiosity to see if there was only a binary situation: either firstname-lastname or whatever in the url in its place. In this tutorial we can read “You can personalize your Acclaim profile URL (e.g. http://www.youracclaim.com/user/your-name)". So this is why our first Ana had a 4-digit number instead of a name. But until I figure this out, I searched around and found something also important. After doing some googling using
site:youracclaim.com/users/* intext:"John Smith",
which is a very common name, I ‘ve found 2-3 acclaim profiles with john-smith.e23bd433 or similar in the link (there is no such profile, it’s just the format I found).
As we see the initial firstname-lastname format still exists in the url and it is followed by a dot and some random(?) alphanumerical string. That means hitting the following google dork, will reveal all searchable profiles of people named “john smith” (except the ones with manipulated urls by their owners):
site:youracclaim.com/users/* inurl:"john-smith"
I ‘ve seen this work even if your target has a middle name, like we did with the last “Ana” above. He/she will still show up in your results. For example, in our case it could be john-rudolf-smith.e23df545.
While experimenting more, I ‘ve found that there were people with usernames in their profile url, instead of names. For example, youracclaim.com/users/sudo/. Meaning you can even try putting a known username of your target in the url and maybe you find his profile. Tools like whatsmyname don’t include this in their searched sites. So, you might find something valuable.
Taking under consideration all of the above, I came to the conclusion that acclaim site has a default format of firstname-lastname, if you are the first user named “John Smith” or w/e and from the second and so on, it uses the format firtsname-lastname.a23fg345 (random alphanumerical of this form – 1 char followed by 2 numbers followed by 2 chars and 3 numbers). If you decide to change it, you can do so through your profile settings. You can switch it to whatever you want, but some people use a nickname instead of something random. Also, most people don’t change anything in the url, in order to keep it “professional”, or just don't care.
Now let’s suppose you somehow know your target has a specific certification like “Microsoft Certified: Azure Solutions Architect Expert” but you can’t find his account. Switch your google searching to
site:youracclaim.com/users/* intext:"Microsoft Certified: Azure Solutions Architect Expert"
then add queries like intext:”x” where x could be a username, a partial username, a partial name, city, country and so on. There are countless ways to find a profile as long as it’s open to search engines.
Now let’s move on to a badge section found in a profile. There is an option under the basic info saying, “Sort by:”, where we can select the “Most recent” option. The badges of the profile will now be reordered in a way that the first one on the top left corner, will be the most recent.
site:youracclaim.com/users/* inurl:"john-smith"
I ‘ve seen this work even if your target has a middle name, like we did with the last “Ana” above. He/she will still show up in your results. For example, in our case it could be john-rudolf-smith.e23df545.
While experimenting more, I ‘ve found that there were people with usernames in their profile url, instead of names. For example, youracclaim.com/users/sudo/. Meaning you can even try putting a known username of your target in the url and maybe you find his profile. Tools like whatsmyname don’t include this in their searched sites. So, you might find something valuable.
Taking under consideration all of the above, I came to the conclusion that acclaim site has a default format of firstname-lastname, if you are the first user named “John Smith” or w/e and from the second and so on, it uses the format firtsname-lastname.a23fg345 (random alphanumerical of this form – 1 char followed by 2 numbers followed by 2 chars and 3 numbers). If you decide to change it, you can do so through your profile settings. You can switch it to whatever you want, but some people use a nickname instead of something random. Also, most people don’t change anything in the url, in order to keep it “professional”, or just don't care.
Now let’s suppose you somehow know your target has a specific certification like “Microsoft Certified: Azure Solutions Architect Expert” but you can’t find his account. Switch your google searching to
site:youracclaim.com/users/* intext:"Microsoft Certified: Azure Solutions Architect Expert"
then add queries like intext:”x” where x could be a username, a partial username, a partial name, city, country and so on. There are countless ways to find a profile as long as it’s open to search engines.
Now let’s move on to a badge section found in a profile. There is an option under the basic info saying, “Sort by:”, where we can select the “Most recent” option. The badges of the profile will now be reordered in a way that the first one on the top left corner, will be the most recent.
Clicking the most recent badge will now take us to another page where we can see when this badge was issued!
This is quite helpful in investigations like the ones in Trace Labs, where it might reveal a date after a person went missing!
Sometimes the “Earning Criteria” section will reveal more info about the target, regarding his job experiences as shown in the two examples below:
Sometimes the “Earning Criteria” section will reveal more info about the target, regarding his job experiences as shown in the two examples below:
Things that now seem of low importance, could be very valuable when investigating a real case. Worst case scenario, they can help you understand what the target’s job is/was if you are not sure about the nature of the particular badge you are looking at.
You can look if an email has been used to create a profile in your acclaim site the old-fashioned way: try creating an account with whatever input, target’s true e-mail and a one-char password like below.
You can look if an email has been used to create a profile in your acclaim site the old-fashioned way: try creating an account with whatever input, target’s true e-mail and a one-char password like below.
Sometimes we might not be able to find the acclaim profile of a target using all of the above techniques. We can still have some hope by switching strategy. Remember that when conducting OSINT investigations, the only limit in finding more leads, is your creativity.
Switch to LinkedIn or similar social media platform (e.g. xing). Try finding your target there. Search under the activity section clicking the “See all activity” button and try to find a post of the target sharing his acclaim badge with others like the post shown below:
Switch to LinkedIn or similar social media platform (e.g. xing). Try finding your target there. Search under the activity section clicking the “See all activity” button and try to find a post of the target sharing his acclaim badge with others like the post shown below:
Another way is to search under the “Licenses & certifications” section of your target’s LinkedIn profile. Most of the times, users will put the link of their badge under the “See credential” button of their corresponding skill/certification.
In some rare cases, you might see the target posting immediately the whole link for this badge in the same section as shown below:
Just click the link to see the badge and the rest are simple. You will be redirected to the badge but just above the badge in the top of the page you will see a link redirecting you to the target’s profile. From there, you can then explore everything we have mentioned such as other social media profiles. Please note that I have also seen multiple times, people posting their acclaim badges in their other social media profiles (e.g. Twitter).
I haven’t figured out yet, possible ways/tricks to reveal emails associated with a public profile. Also, I couldn’t find any trick using the developer tools. If I find anything on these two, I will update this guide.
What more can we reveal from this platform? Maybe find all intelligence analysts of different countries trained by NATO using:
site:youracclaim.com/users/* "nato school Oberammergau" as a google query?
What else can you thing of? Drop me a message if you ‘d like in twitter.
Key takeaways (aka tl;dr)
- Digital badges can provide a wealth of information in OSINT investigations. They can provide images, usernames, place of residence or studies, profile pictures, social media accounts and more.
- Try using google dorks that include the format “firstname-lastname” or “nickname” in order to find searchable acclaim profiles.
- If your google results don’t include your target, try to manipulate the url including “firstname-lastname” or “nickname” of your target, after the “user/” part. Your target’s profile might be publicly accessible but not searchable. The more unique your target’s name is, the better for you, since there won’t be many people using this combination of first name – last name.
- Try all available search engines (Google, Yandex, Bing etc). Each might yield another result which was hidden by another. Remember to use different variations of the site: search parameter.
- Use the “Sort by: Most recent” feature to find the last (training) activity of your target.
- Look at the badges’ earning criteria for further information that can be revealed.
- If you can’t find your target’s acclaim profile, try searching for his LinkedIn (or similar site) profile, since he/she might have already posted a link there.
- Experiment with other digital badge sites to get a grasp on how you can reveal the profiles of their users. If you find a way, make a post to let the community know about it.
Thanks for reading! Until next time, stay healthy!
Do you have a question/comment regarding this methodology? Please e-mail me at theinspector32@protonmail.com, or send me a message on twitter.
What more can we reveal from this platform? Maybe find all intelligence analysts of different countries trained by NATO using:
site:youracclaim.com/users/* "nato school Oberammergau" as a google query?
What else can you thing of? Drop me a message if you ‘d like in twitter.
Key takeaways (aka tl;dr)
- Digital badges can provide a wealth of information in OSINT investigations. They can provide images, usernames, place of residence or studies, profile pictures, social media accounts and more.
- Try using google dorks that include the format “firstname-lastname” or “nickname” in order to find searchable acclaim profiles.
- If your google results don’t include your target, try to manipulate the url including “firstname-lastname” or “nickname” of your target, after the “user/” part. Your target’s profile might be publicly accessible but not searchable. The more unique your target’s name is, the better for you, since there won’t be many people using this combination of first name – last name.
- Try all available search engines (Google, Yandex, Bing etc). Each might yield another result which was hidden by another. Remember to use different variations of the site: search parameter.
- Use the “Sort by: Most recent” feature to find the last (training) activity of your target.
- Look at the badges’ earning criteria for further information that can be revealed.
- If you can’t find your target’s acclaim profile, try searching for his LinkedIn (or similar site) profile, since he/she might have already posted a link there.
- Experiment with other digital badge sites to get a grasp on how you can reveal the profiles of their users. If you find a way, make a post to let the community know about it.
Thanks for reading! Until next time, stay healthy!
Do you have a question/comment regarding this methodology? Please e-mail me at theinspector32@protonmail.com, or send me a message on twitter.



















Did you know that you can also combine reverse image search (for a certification logo, for example) with the site: operator? Examples here https://booleanstrings.com/2020/08/12/hack-find-linkedin-members-by-company-size/
ReplyDeleteOnline Casino - Play Online Casino | Shootercasino
ReplyDeletePlay online casino games for 인카지노 fun or for real money. choegocasino Enjoy 제왕 카지노 the best online casino games for real money right here at Shootercasino!