Skype – A hidden OSINT goldmine
I have previously posted about skype potential uses in OSINT investigations in one of my #DailyOSINT tweets, but I decided to provide a more in-depth guide to show everyone in the OSINT community the true potential of this application. I have seen no one talk about it in the OSINT community and I think it’s about time we understand the possibilities it provides.
Skype is an application designed for communication and e-conferencing between its users. It is widely spread with a vast user base. Although it has begun losing popularity with the rise of alternative tools such as zoom etc, it still dominates its sector for a long time, and this means that your target is very likely to have a Skype account. Let’s look at some rough numbers:
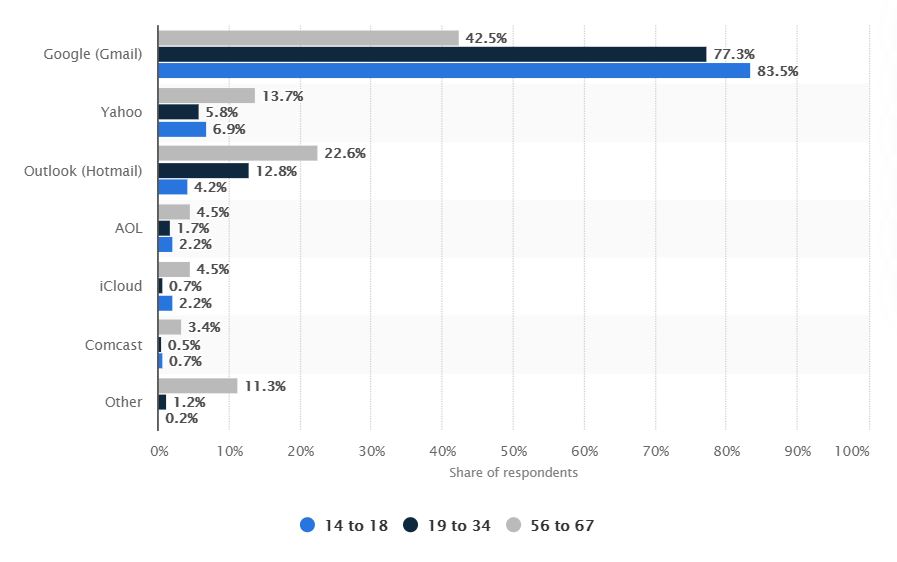
According to Statista, this is the percentage of U.S. internet users who use Skype as of January 2018, by age group:
According to Statista, this is the percentage of U.S. internet users who use Skype as of January 2018, by age group:
Also, according to the same site, the number of estimated Skype users registered worldwide from 2009 to 2024 is constantly growing with a forecast for 2024, estimating around 2.4 billion total users.
Another article states that Skype for Business holds the first rank, with a 57% share, of all six major platforms for web-conferencing. The list goes on forever and you can search around yourself with a simple google search.
Skype has a web version, a downloadable app version and a mobile version, all providing the same functions. If for any reason you don’t want or can’t have an investigative Skype account, you can use the Skypli site, but be aware that you will lose a function that skype apps have (I will explain below).
Skype allows you to query:
1. A full name (e.g. John Smith)
2. A username (e.g. dragon32)
3. An e-mail address (e.g. jsmith@yahoo.com)
4. A telephone number
The above list alone should have shock you already, but in the slim change it hasn’t, please keep on reading as I further explain myself. I will be using the Skype windows app for demonstration, but you can use whatever suits you. The methodologies remain the same.
Querying skype using full name
Click inside the search bar as seen below
Another article states that Skype for Business holds the first rank, with a 57% share, of all six major platforms for web-conferencing. The list goes on forever and you can search around yourself with a simple google search.
Skype has a web version, a downloadable app version and a mobile version, all providing the same functions. If for any reason you don’t want or can’t have an investigative Skype account, you can use the Skypli site, but be aware that you will lose a function that skype apps have (I will explain below).
Skype allows you to query:
1. A full name (e.g. John Smith)
2. A username (e.g. dragon32)
3. An e-mail address (e.g. jsmith@yahoo.com)
4. A telephone number
The above list alone should have shock you already, but in the slim change it hasn’t, please keep on reading as I further explain myself. I will be using the Skype windows app for demonstration, but you can use whatever suits you. The methodologies remain the same.
Querying skype using full name
Click inside the search bar as seen below
Now search for your target’s full name -first name followed by last name or vice versa it doesn’t really matter- and a list with ALL Skype profiles using this display name will show up, even if the target is not in your friends list.
Note that the display name is different from the Skype username, which we will examine in a while. The display name is determined by each user and can be modified anytime, whereas the username is automatically configured by Skype and can never change. Just for testing purposes here is a list showing up when searching for John Smith:
Note that the display name is different from the Skype username, which we will examine in a while. The display name is determined by each user and can be modified anytime, whereas the username is automatically configured by Skype and can never change. Just for testing purposes here is a list showing up when searching for John Smith:
Even if you don’t know or you are not sure about the whole name of your target, you can begin filling the search bar and Skype will pop user suggestions, which is quite handy in OSINT investigations when we only know only a part of the target’s full name. Below is an example of a partial name search and suggestions that pop.
You see there was only one exact match for our query, but all others had a middle name or a last name that we might not have known (depends if dolor was middle or last name). So, we found extra leads based on a partial name! The same could happen if our input was a single last name – unknown first name(s) could be revealed.
Now let’s click on a Smith profile that came up, so that we can see what information we can find.
Now let’s click on a Smith profile that came up, so that we can see what information we can find.
So now we know his skype username which ends in 4198 (wanna bet this is a birth date?), and a place of residence (either current or past one) that includes both a country and a state. Not bad. Some people actually put their birthday public for everyone to see like the one seen below:
Now, we can’t really use his profile image but that’s ok because there is a workaround. Visit https://avatar.skype.com/v1/avatars/username/public and change the username part with the username of your target. In case there is a live: in the username, include that also in the link. If we do that for our target, we get the following picture opened in a new tab.
This image can then be downloaded, or reverse searched easily. It might then lead us to other social media profiles for this user. Unfortunately, Skype strips all exif data from photos, or at least I could not find an image with preserved exif data, after several different tests I performed.
So, with only a (partial or full) name(!) we may now have:
- A middle or last name we might not have known
- A username, which the target might use in other applications/sites also
- A present or future place of residence, with accuracy of at least country and at best city, narrowing down our search extremely
- A birth date or a reliable clue about it
- A profile image to reverse search or analyze.
I don’t know many free tools/apps that can provide so many information for a target with a single name as input. Moving on.
Using skype usernames to find hidden information
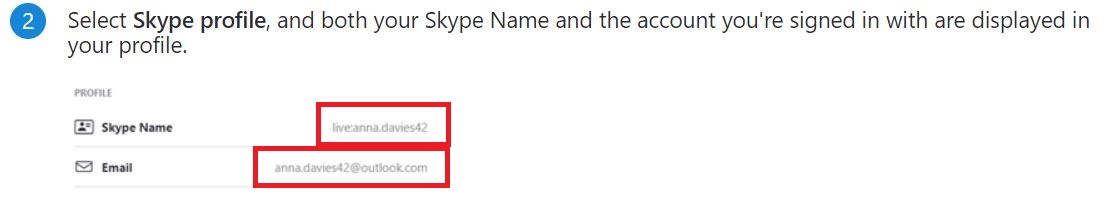
Although the display names, which we looked at above, can be edited by the users at any time, this is not the case with users’ Skype usernames. We can confirm that by looking at the Skype’s support page, as shown below. Skype uses the term “Skype names” for its usernames, so don’t get confused.
So, with only a (partial or full) name(!) we may now have:
- A middle or last name we might not have known
- A username, which the target might use in other applications/sites also
- A present or future place of residence, with accuracy of at least country and at best city, narrowing down our search extremely
- A birth date or a reliable clue about it
- A profile image to reverse search or analyze.
I don’t know many free tools/apps that can provide so many information for a target with a single name as input. Moving on.
Using skype usernames to find hidden information
Although the display names, which we looked at above, can be edited by the users at any time, this is not the case with users’ Skype usernames. We can confirm that by looking at the Skype’s support page, as shown below. Skype uses the term “Skype names” for its usernames, so don’t get confused.
Let’s analyze a little bit what we learn from here:
1. The user’s Skype username is autogenerated by Skype (user cannot create/select it himself) during account creation
2. A user can never change/modify his username
3. If a user wants to change his username, he must create a new account
4. If a user deletes his account, his Microsoft account is also deleted (thus discouraging people to do so)
Now let’s look something really interesting about usernames in another Skype support page:
1. The user’s Skype username is autogenerated by Skype (user cannot create/select it himself) during account creation
2. A user can never change/modify his username
3. If a user wants to change his username, he must create a new account
4. If a user deletes his account, his Microsoft account is also deleted (thus discouraging people to do so)
Now let’s look something really interesting about usernames in another Skype support page:
I want you to take a look at something very specific. Look at the example and compare the username given to the user with the e-mail address you see (that was supposedly used for registration). Do you see any correlation? Correct. The username of the user’s e-mail address (everything before the @ symbol) is exactly the same as his skype username!
Now let’s switch to our "john smith" search again. Among other profiles, we see the one below:
Now let’s switch to our "john smith" search again. Among other profiles, we see the one below:
So, all we know from this is his Skype username and nothing else. Correct? WRONG! We basically know the username used in the e-mail address he used to register to Skype! Why is this important? We can official brute force “guess” this man’s email address!!! Let’s try it. Switch to a google search of most famous/top e-mail providers in the US and UK, since he has a lot more chances of coming from these countries (other profiles just state publicly where they come from, remember? We don’t even need to guess for those). We get this result for the US:
Now let’s start guessing using gmail.com first, then yahoo.com then outlook.com and so on. In our fifth try, we discover that the same user’s profile is found again under one of our e-mail address guesses! We basically found his e-mail address in seconds!
This technique works for all usernames using “live:” followed by a username. But what happens when we have a “live:” followed by a random set of strings in the Skype username?
First of all, why is there such a differentiation in the username formats? A volunteer moderator in a Microsoft forum gives us the answer:
So according to this, depending on the time of registration and the way of registration, each user gets a different Skype username. Let’s see now if we can dig deeper. According to an answer in quora:
So, we verify once more that the part after live: is indeed used in the e-mail a user has registered in Skype. But we also see, that if someone else also has an e-mail address starting with the same username, skype attaches an underscore followed by a number next to your username to distinguish these different profiles. Can we verify this? Of course we can (I already did it for you).
Although we have triple checked that email username is inherited by skype username, this profile doesn’t follow this rule. Does this mean it’s the 103rd account using that email username? I hope not but it seems legit. In any case, that teaches us that whenever we see an underscore followed by number(s), we know that it’s irrelevant in e-mail search of the user.
The last answer we saw on quora, gave us also another hint:
Skype accounts that contain live: followed by a stupid random long string of numbers and letters, are the ones that used their mobile phone numbers to register to skype, rather than their e-mail address. It is also stated that this is a pseudo-number and has no link to any information. Is this true? Probably yes. I tried converting some usernames in hexadecimal format and I all I got is unreadable texts like 6�t�.
In the same quora page, the same user continues his respond saying:
The last answer we saw on quora, gave us also another hint:
Skype accounts that contain live: followed by a stupid random long string of numbers and letters, are the ones that used their mobile phone numbers to register to skype, rather than their e-mail address. It is also stated that this is a pseudo-number and has no link to any information. Is this true? Probably yes. I tried converting some usernames in hexadecimal format and I all I got is unreadable texts like 6�t�.
In the same quora page, the same user continues his respond saying:
then ends his response saying:
To be honest with you, I haven’t found a credible source confirming all of these. I have only found people that believe this is the indeed the case. The volunteer admin of the Microsoft forum gave a similar answer to this. The author of the quora post mentions in his bio: “I do video calling products/services for elderly & impaired”. Is that enough to verify this info? No. but this is the best I got.
Since I found no evidence disproving all of these and many different users are backing this info (I found more than what you see here), I ‘ll take it. I am not saying you should to, but if you find anything that disproves this theory, you can let me know.
So, we pretty much learned that we can roughly determine the age and type of a Skype account, according to the following:
1) if you made your account before around 2016, you have an id without live: inside it, since you could create w/e ID you wanted yourself
2) if you made your account after around 2016 and you used an e-mail to register to Skype, you have an id which looks like this: live:{username of your e-mail}
3) if you made your account after around 2016 and you used a telephone number to register to Skype, you have an id which looks like this: live:{random hexadecimal pseudo-number}
4) if you made your account after late 2019, you have an id which looks like this: live:.cid.{random hexadecimal pseudo-number}
This ID is somehow linked to your Microsoft account also, but I have not investigated much to find a connection to help in OSINT investigations and will let you know if I find something in the future.
There are many usages of this but I can think of one right away: If your target has something like 2003 at the end of his username/email address and his ID format is the first type (without live: inside it), then it is highly unlikely this indicates his birth year because he would be 13 years old on 2016 (which is the latest to have this id format) and it is very difficult for a 13-year-old to have a skype account (not impossible though). If you just looked at this account without this information, it would feel right because in 2021 this guy would be 18 years old, which makes sense (to have a skype account).
Moving on, I would like to point out one last thing that skype usernames can help you with. If you remember, one of our targets had a username of "tigerheart777". I believe this is a unique one, but some of you may argue with that. In any case, let’s run a search for that on skype.
Since I found no evidence disproving all of these and many different users are backing this info (I found more than what you see here), I ‘ll take it. I am not saying you should to, but if you find anything that disproves this theory, you can let me know.
So, we pretty much learned that we can roughly determine the age and type of a Skype account, according to the following:
1) if you made your account before around 2016, you have an id without live: inside it, since you could create w/e ID you wanted yourself
2) if you made your account after around 2016 and you used an e-mail to register to Skype, you have an id which looks like this: live:{username of your e-mail}
3) if you made your account after around 2016 and you used a telephone number to register to Skype, you have an id which looks like this: live:{random hexadecimal pseudo-number}
4) if you made your account after late 2019, you have an id which looks like this: live:.cid.{random hexadecimal pseudo-number}
This ID is somehow linked to your Microsoft account also, but I have not investigated much to find a connection to help in OSINT investigations and will let you know if I find something in the future.
There are many usages of this but I can think of one right away: If your target has something like 2003 at the end of his username/email address and his ID format is the first type (without live: inside it), then it is highly unlikely this indicates his birth year because he would be 13 years old on 2016 (which is the latest to have this id format) and it is very difficult for a 13-year-old to have a skype account (not impossible though). If you just looked at this account without this information, it would feel right because in 2021 this guy would be 18 years old, which makes sense (to have a skype account).
Moving on, I would like to point out one last thing that skype usernames can help you with. If you remember, one of our targets had a username of "tigerheart777". I believe this is a unique one, but some of you may argue with that. In any case, let’s run a search for that on skype.
We can see here that one more person is using this username apart from our Smith. If we run a query on whatsmyname we might find more than one profiles with that username. Information we have found on this Skype search, allows us to know there are actually two persons using this username and help us decide who matches best to other profiles. For example, if one of them is a woman and our smith is a man, certain profiles that could fit more to a woman target, will be easier excluded in our investigation.
Searching skype for e-mail addresses
If your only information about a target is an e-mail address and he has a Skype Account linked to it, you can immediately find at least a full name and/or a username he uses. And this is sometimes more than enough to advance your investigation much further than having a single e-mail address. But remember, even if you get practically nothing as a result, you have verified that this e-mail address most probably exists.
There are some more things to consider though. University and work e-mail addresses often need verification and using skype is a great way to verify these exist. There are two reasons for this:
First, Skype is linked to Microsoft Teams. Microsoft Teams is becoming more and more popular with companies and universities due to its great capabilities in teamwork and e-conferencing capabilities.
Second, there is a Skype version for Businesses, which I assume businesses use to support more people on a call and some extra handy capabilities.
That said, an OSINT investigator can:
- Easily verify student e-mail addresses, since students are often instructed to use their e-mail addresses to Teams or Skype for Businesses for online classes and other purposes, such as exams.
- Search if an e-mail address (work or student) has been used to create a Microsoft Teams account (if the target e-mail has not been used for a Skype account) to both verify the existence of the e-mail address and reveal if there is a Teams account linked to it. If there is, you will get a result like below:
Searching skype for e-mail addresses
If your only information about a target is an e-mail address and he has a Skype Account linked to it, you can immediately find at least a full name and/or a username he uses. And this is sometimes more than enough to advance your investigation much further than having a single e-mail address. But remember, even if you get practically nothing as a result, you have verified that this e-mail address most probably exists.
There are some more things to consider though. University and work e-mail addresses often need verification and using skype is a great way to verify these exist. There are two reasons for this:
First, Skype is linked to Microsoft Teams. Microsoft Teams is becoming more and more popular with companies and universities due to its great capabilities in teamwork and e-conferencing capabilities.
Second, there is a Skype version for Businesses, which I assume businesses use to support more people on a call and some extra handy capabilities.
That said, an OSINT investigator can:
- Easily verify student e-mail addresses, since students are often instructed to use their e-mail addresses to Teams or Skype for Businesses for online classes and other purposes, such as exams.
- Search if an e-mail address (work or student) has been used to create a Microsoft Teams account (if the target e-mail has not been used for a Skype account) to both verify the existence of the e-mail address and reveal if there is a Teams account linked to it. If there is, you will get a result like below:
The icon has changed to this search results from a skype to a Microsoft Teams one.
Note: This cannot be done with the skypli site.
Another useful thing you need to know about searching with e-mail addresses is that if you type a very generic e-mail address, results can reach even 100+ in numbers. If you try searching for “whatever@yahoo.com” then you get such an absurd number of results. This can help you find that all these profiles have used a troll e-mail address on registration. And now that we know the methodology above, we can easily conclude that profiles with live:whatever_{number} may also be using troll e-mails.
Using telephone numbers in a skype search
Skype constantly asks users to add their phone numbers if they haven’t done so. I suppose this is part of its marketing, because there are ways to use skype to call real phone numbers. Suppose you have a telephone number, which you think might belong or belonged to your target at some point. You can search Skype and find out if his name pops up to verify this connection. Or imagine that you only have a phone number to begin your investigation and its tied to a Skype account. Now you have a name or a username to further advance your search.
Important: Skype accepts phone number search queries that include country code in +1 format and not in 001 format (e.g. +12025550117 for US)
In conclusion, Skype can be a great free OSINT tool, although not mentioned often in the OSINT community. I hope in this blog post, I could show you a little bit why. Don't forget that people tend to use their true personal details in these applications because they are using them for more formal reasons (job, studies etc)
That’s all folks! I hope the length of the text didn’t tire you and that you learned something new.
Until next time, stay healthy!
Do you have a question/comment regarding this methodology? Please e-mail me at theinspector32@protonmail.com,or send me a message on twitter.
Note: This cannot be done with the skypli site.
Another useful thing you need to know about searching with e-mail addresses is that if you type a very generic e-mail address, results can reach even 100+ in numbers. If you try searching for “whatever@yahoo.com” then you get such an absurd number of results. This can help you find that all these profiles have used a troll e-mail address on registration. And now that we know the methodology above, we can easily conclude that profiles with live:whatever_{number} may also be using troll e-mails.
Using telephone numbers in a skype search
Skype constantly asks users to add their phone numbers if they haven’t done so. I suppose this is part of its marketing, because there are ways to use skype to call real phone numbers. Suppose you have a telephone number, which you think might belong or belonged to your target at some point. You can search Skype and find out if his name pops up to verify this connection. Or imagine that you only have a phone number to begin your investigation and its tied to a Skype account. Now you have a name or a username to further advance your search.
Important: Skype accepts phone number search queries that include country code in +1 format and not in 001 format (e.g. +12025550117 for US)
In conclusion, Skype can be a great free OSINT tool, although not mentioned often in the OSINT community. I hope in this blog post, I could show you a little bit why. Don't forget that people tend to use their true personal details in these applications because they are using them for more formal reasons (job, studies etc)
That’s all folks! I hope the length of the text didn’t tire you and that you learned something new.
Until next time, stay healthy!
Do you have a question/comment regarding this methodology? Please e-mail me at theinspector32@protonmail.com,or send me a message on twitter.




















Very helpful, than you kind sir.
ReplyDeleteThis is an informative blog. Keep it up. I am looking forward to this kind of blog. I took a lot away from this blog. also, your thoughts were very well organized as far as how you went into details and made it very. Thanks
ReplyDeleteGoogle bellen
Thanks for giving the information. This blog is very helpful. I learned a lot from this I hope you will keep sharing such information in the future also.
ReplyDeletevisit site
The Best Casino Apps in Arizona 2021 | JamBase
ReplyDeletePlay on your mobile device. · Play a variety of 계룡 출장안마 games, 구리 출장샵 including 파주 출장안마 slots, blackjack, roulette, craps, and roulette with real money. · 양주 출장마사지 Get 김해 출장마사지 up to a $1000
I think this is among the most vital info for me.
ReplyDeleteAnd i am glad reading your article. But wanna remark on few general things,
The website style is great, the articles is really excellent..............PayPal Bellen Nederland